Windows Server Rights Management
Active Directory Rights Management Services (AD RMS) is a Microsoft Windows security tool that provides persistent data protection by enforcing data access policies. For documents to be protected. Installing AD RMS in Windows Server 2016. In order to install the Active Directory Rights Management Services (AD RMS) role, you need to perform the following steps: On DC1, using the Server Manager console, launch the Add Roles and Features Wizard. Click Next and accept the default selections till the Select server roles page displays. Microsoft Windows Rights Management Services (RMS) for Windows Server 2003 offers a solution. RMS, which is based on Extensible Rights Markup Language (XrML) 1.2.1, consists of a client component and a server component that work in tandem with RMS-aware applications to let users protect document, email message, or Web site content. Apr 18, 2005 Windows Rights Management Services (RMS) 1.0 Service Pack 1 (SP1) for Microsoft Windows Server 2003, a security service for Windows Server 2003, is information protection that works with RMS-enabled applications to help safeguard digital information from unauthorized use – both online and offline, inside and outside of the firewall. In this, Part 1 of our series on the evolution of Active Directory Rights Management Services, we provid an overview of what RMS is, how it works and some of the changes it has undergone from its release as an add-on for Windows Server 2003 back in 2005 to its incarnation in Windows Server 2012. You can configure the user rights assignment settings in the following location within the Group Policy Management Console (GPMC) under Computer Configuration Windows Settings Security Settings Local Policies User Rights Assignment, or on the local device by using the Local Group Policy Editor (gpedit.msc).
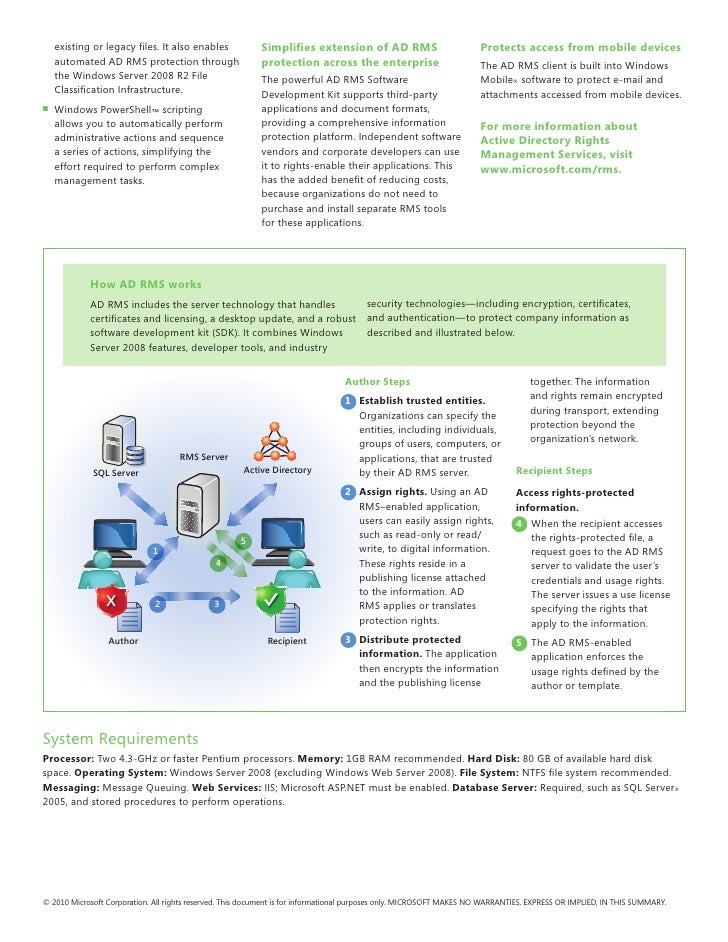
Active Directory Rights Management Services (AD RMS, known as Rights Management Services or RMS before Windows Server 2008) is a server software for information rights management shipped with Windows Server. It uses encryption and a form of selective functionality denial for limiting access to documents such as corporate e-mails, Microsoft Word documents, and web pages, and the operations authorized users can perform on them. Companies can use this technology to encrypt information stored in such document formats, and through policies embedded in the documents, prevent the protected content from being decrypted except by specified people or groups, in certain environments, under certain conditions, and for certain periods of time. Specific operations like printing, copying, editing, forwarding, and deleting can be allowed or disallowed by content authors for individual pieces of content, and RMS administrators can deploy RMS templates that group these rights together into predefined rights that can be applied en masse.
RMS debuted in Windows Server 2003, with client API libraries made available for Windows 2000 and later. The Rights Management Client is included in Windows Vista and later, is available for Windows XP, Windows 2000 or Windows Server 2003.[1] In addition, there is an implementation of AD RMS in Office for Mac to use rights protection in OS X and some third-party products are available to use rights protection on Android, Blackberry OS, iOS and Windows RT.[2][3]
Attacks against policy enforcement capabilities[edit]
In April 2016, an alleged attack on RMS implementations (including Azure RMS) was published and reported to Microsoft.[4][5] The published code allows an authorized user that has been granted the right to view an RMS protected document to remove the protection and preserve the file formatting. This sort of manipulation requires that the user has been granted rights to decrypt the content to be able to view it. While Rights Management Services makes certain security assertions regarding the inability for unauthorized users to access protected content, the differentiation between different usage rights for authorized users is considered part of its policy enforcement capabilities, which Microsoft claims to be implemented as 'best effort', so it is not considered by Microsoft to be a security issue but a policy enforcement limitation. Previously the RMS SDK enforced signing of code using the RMS capabilities in order to provide some level of control on which applications interacted with RMS, but this capability was later removed due to its limited ability to restrict such behaviors given the possibility to write applications use the web services directly to obtain licenses to decrypt the content. [6]
In addition, using this same technique, a user that has been granted rights to view a protected document can manipulate the content of the document without leaving traces of the manipulation. Since Azure RMS is not a non-repudiation solution and, unlike document signing solutions, does not claim to provide anti-tampering capabilities, and since the changes can only be made by users that are granted rights to the document, Microsoft does not consider the later issue to be an actual attack against the claimed capabilities of RMS. [7]The researchers provide a proof of concept tool, to allow evaluation of the results, via GitHub.[8]
Software support[edit]
RMS is natively supported by the following products:
- Microsoft Office 2003 and later: Word, Excel, PowerPoint, Outlook, InfoPath[9]
- Microsoft Office for Mac 2011 and later: Word, Excel, PowerPoint, Outlook
- SharePoint 2007 and later
- Exchange Server 2007 and later
- XML Paper Specification (XPS)
Third-party solutions, such as those from Secure Islands (acquired by Microsoft), GigaTrust and Liquid Machines (acquired by Check Point) can add RMS support to the following:
- SharePoint 2003[10][11][12]
- Microsoft Project[13][12]
- Adobe Acrobat[14][15][12][16]
- IIS 6.0
See also[edit]
References[edit]
- ^Microsoft Windows Rights Management Services Client with Service Pack 2 - x86
- ^http://www.rmsviewer.com/
- ^'Archived copy'. Archived from the original on 2012-10-31. Retrieved 2013-10-14.CS1 maint: archived copy as title (link)
- ^Mainka, Christian; Grothe, Martin (2016-08-01). 'How to Break Microsoft Rights Management Services'. On Web-Security and -Insecurity. Network and Data Security Chair Ruhr-University Bochum. Retrieved 2016-08-04.
- ^Mainka, Christian; Grothe, Martin (2016-08-04). 'How to Break Microsoft Rights Management Services'. WOOT '16 - 10 USENIX Workshop on Offensive Technologies. USENIX Security Symposium. Retrieved 2016-08-04.
- ^'Creating a Rights Management Manifest'. Microsoft Development Network. Microsoft. Retrieved 2017-10-06.
- ^'AD RMS FAQ'. MicrosoftDocs. Microsoft. Retrieved 2017-10-06.
- ^Mainka, Christian; Grothe, Martin (2016-07-07). 'MS-RMS-Attacks'. MS-RMS-Attacks. GitHub. Retrieved 2016-08-04.
- ^'Plan Information Rights Management in Office 2013'. TechNet. Retrieved 2015-11-24.
- ^'Archived copy'. Archived from the original on 2013-02-02. Retrieved 2010-07-13.CS1 maint: archived copy as title (link)
- ^'Archived copy'. Archived from the original on 2013-02-16. Retrieved 2013-01-31.CS1 maint: archived copy as title (link)
- ^ abc'GigaTrust Announces Availability of Adobe® Rights-Management Protector for Microsoft® Office SharePoint Server 2007 (MOSS 2007)'. Archived from the original on 2008-05-17. Retrieved 2009-02-18.
- ^'Archived copy'. Archived from the original on 2013-02-02. Retrieved 2010-07-13.CS1 maint: archived copy as title (link)
- ^'Archived copy'. Archived from the original on 2013-02-16. Retrieved 2013-01-31.CS1 maint: archived copy as title (link)
- ^http://www.prnewswire.com/news-releases/gigatrust-launches-new-rms-desktop-pdf-client-for-adobe-with-comprehensive-reporting-auditing-and-compliance-capability-277422531.html
- ^http://www.foxitsoftware.com/products/rms/
External links[edit]

Applies to: Azure Information Protection, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012, Windows Server 2008 R2
Windows Server Rights Management Definition
Use the following information to help you configure your on-premises servers that will use the Azure Rights Management (RMS) connector. These procedures cover step 5 from Deploying the Azure Rights Management connector.
Before you begin, make sure that you have installed and configured the RMS connector and you have checked any prerequisites that are applicable for the servers that will use the connector.
Configuring servers to use the RMS connector
After you have installed and configured the RMS connector, you are ready to configure your on-premises servers that will connect to the Azure Rights Management service and use this protection technology by using the connector. This means configuring the following servers:
For Exchange 2016 and Exchange 2013: Client access servers and mailbox servers
For Exchange 2010: Client access servers and hub transport servers
For SharePoint: Front-end SharePoint webservers, including those hosting the Central Administration server
For File Classification Infrastructure: Windows Server computers that have installed File Resource Manager
This configuration requires registry settings. To do this, you have two options: Automatically by using the server configuration tool for Microsoft RMS connector, or manually by editing the registry.
Automatically by using the server configuration tool for Microsoft RMS connector:
Advantages:
No direct editing of the registry. This is automated for you by using a script.
No need to run a Windows PowerShell cmdlet to obtain your Microsoft RMS URL.
The prerequisites are automatically checked for you (but not automatically remediated) if you run it locally.
Disadvantages:
- When you run the tool, you must make a connection to a server that is already running the RMS connector.
Manually by editing the registry:
Advantages:
- No connectivity to a server running the RMS connector is required.
Disadvantages:
More administrative overheads that are error-prone.
You must obtain your Microsoft RMS URL, which requires you to run a Windows PowerShell command.
You must always make all the prerequisites checks yourself.
Important
In both cases, you must manually install any prerequisites and configure Exchange, SharePoint, and File Classification Infrastructure to use Rights Management.
For most organizations, automatic configuration by using the server configuration tool for Microsoft RMS connector will be the better option, because it provides greater efficiency and reliability than manual configuration.
After making the configuration changes on these servers, you must restart them if they are running Exchange or SharePoint and previously configured to use AD RMS. There is no need to restart these servers if you are configuring them for Rights Management for the first time. You must always restart the file server that is configured to use File Classification Infrastructure after you make these configuration changes.
How to use the server configuration tool for Microsoft RMS connector
If you haven’t already downloaded the script for the server configuration tool for Microsoft RMS connector (GenConnectorConfig.ps1), download it from the Microsoft Download Center.
Save the GenConnectorConfig.ps1 file on the computer where you will run the tool. If you will run the tool locally, this must be the server that you want to configure to communicate with the RMS connector. Otherwise, you can save it on any computer.
Decide how to run the tool:
Locally: You can run the tool interactively, from the server to be configured to communicate with the RMS connector. This is useful for a one-off configuration, such as a testing environment.
Software deployment: You can run the tool to produce registry files that you then deploy to one or more relevant servers by using a systems management application that supports software deployment, such as System Center Configuration Manager.
Group Policy: You can run the tool to produce a script that you give to an administrator who can create Group Policy objects for the servers to be configured. This script creates one Group Policy object for each server type to be configured, which the administrator can then assign to the relevant servers.
Note
This tool configures the servers that will communicate with the RMS connector and that are listed at the beginning of this section. Do not run this tool on the servers that run the RMS connector.
Start Windows PowerShell with the Run as an administrator option, and use the Get-help command to read instructions how to the use the tool for your chosen configuration method:
To run the script, you must enter the URL of the RMS connector for your organization. Enter the protocol prefix (HTTP:// or HTTPS://) and the name of the connector that you defined in DNS for the load balanced address of your connector. For example, https://connector.contoso.com. The tool then uses that URL to contact the servers running the RMS connector and obtain other parameters that are used to create the required configurations.
Important
When you run this tool, make sure that you specify the name of the load-balanced RMS connector for your organization and not the name of a single server that runs the RMS connector service.
Use the following sections for specific information for each service type:
Note
After these servers are configured to use the connector, client applications that are installed locally on these servers might not work with RMS. When this happens, it is because the applications try to use the connector rather than use RMS directly, which is not supported.
In addition, if Office 2010 is installed locally on an Exchange server, the client app’s IRM features might work from that computer after the server is configured to use the connector, but this is not supported.
In both scenarios, you must install the client applications on separate computers that are not configured to use the connector. They will then correctly use RMS directly.
Configuring an Exchange server to use the connector
The following Exchange roles communicate with the RMS connector:
For Exchange 2016 and Exchange 2013: Client access server and mailbox server
For Exchange 2010: Client access server and hub transport server
To use the RMS connector, these servers running Exchange must be running one of the following software versions:
Exchange Server 2016
Exchange Server 2013 with Exchange 2013 Cumulative Update 3
Exchange Server 2010 with Exchange 2010 Service Pack 3 Rollup Update 6
You will also need on these servers, a version 1 of the RMS client (also known as MSDRM) that includes support for RMS Cryptographic Mode 2. All Windows operating systems include the MSDRM client but early versions of the client did not support Cryptographic Mode 2. If your Exchange servers are running at least Windows Server 2012, no further action is required because the RMS client installed with these operating systems natively supports Cryptographic Mode 2.
If your Exchange servers are running an earlier version of the operating system, verify that the installed version of the RMS client supports Cryptographic Mode 2. To do this, check your installed file version of WindowsSystem32Msdrm.dll against the version numbers listed in the following knowledge-based articles. If the version number installed is the same or higher than the version numbers listed, no further action is required. If the version number installed is lower, download and install the hotfix from the article.
Windows Server 2008: https://support.microsoft.com/kb/2627272
Windows Server 2008 R2: https://support.microsoft.com/kb/2627273
Important
If these versions or later versions of Exchange and the MSDRM client are not installed, you will not be able to configure Exchange to use the connector. Check that these versions are installed before you continue.
To configure Exchange servers to use the connector
Make sure that the Exchange servers are authorized to use the RMS connector, by using the RMS connector administration tool and the information from the Authorizing servers to use the RMS connector section. This configuration is required so that Exchange can use the RMS connector.
On the Exchange server roles that communicate with the RMS connector, do one of the following:
Run the server configuration tool for Microsoft RMS connector. For more information, see How to use the server configuration tool for Microsoft RMS connector in this article. Apk installer for windows 10.
For example, to run the tool locally to configure a server running Exchange 2016 or Exchange 2013:
Make manual registry edits by using the information in Registry settings for the RMS connector to manually add registry settings on the servers.
Enable IRM functionality for Exchange by using the Exchange PowerShell cmdlet Set-IRMConfiguration and set
InternalLicensingEnabled $trueandClientAccessServerEnabled $true.
Configuring a SharePoint server to use the connector
The following SharePoint roles communicate with the RMS connector:
- Front-end SharePoint webservers, including those hosting the Central Administration server
To use the RMS connector, these servers running SharePoint must be running one of the following software versions:
SharePoint Server 2016
SharePoint Server 2013
SharePoint Server 2010
A server running SharePoint 2016 or SharePoint 2013 must also be running a version of the MSIPC client 2.1 that is supported with the RMS connector. To make sure that you have a supported version, download the latest client from the Microsoft Download Center.
Warning
There are multiple versions of the MSIPC 2.1 client, so make sure that you have version 1.0.2004.0 or later.
You can verify the client version by checking the version number of MSIPC.dll, which is located in Program FilesActive Directory Rights Management Services Client 2.1. The properties dialog box shows the version number of the MSIPC 2.1 client.
Servers running SharePoint 2010 must have installed a version of the MSDRM client that includes support for RMS Cryptographic Mode 2. The minimum version that is supported in Windows Server 2008 is included in the hotfix that you can download from RSA key length is increased to 2048 bits for AD RMS in Windows Server 2008 R2 and in Windows Server 2008, and the minimum version for Windows Server 2008 R2 can be downloaded from RSA key length is increased to 2048 bits for AD RMS in Windows 7 or in Windows Server 2008 R2. Windows Server 2012 and Windows Server 2012 R2 natively support Cryptographic Mode 2.
To configure SharePoint servers to use the connector
Make sure that the SharePoint servers are authorized to use the RMS connector, by using the RMS connector administration tool and the information from the Authorizing servers to use the RMS connector section. This configuration is required so that your SharePoint servers can use the RMS connector.
On the SharePoint servers that communicate with the RMS connector, do one of the following:
Run the server configuration tool for Microsoft RMS connector. For more information, see How to use the server configuration tool for Microsoft RMS connector in this article.
For example, to run the tool locally to configure a server running SharePoint 2016 or SharePoint 2013:
If you are using SharePoint 2016 or SharePoint 2013, make manual registry edits by using the information in Registry settings for the RMS connector to manually add registry settings on the servers.
Enable IRM in SharePoint. For more information, see Configure Information Rights Management (SharePoint Server 2010) in the SharePoint library.
When you follow these instructions, you must configure SharePoint to use the connector by specifying Use this RMS server, and then enter the load-balancing connector URL that you configured. Enter the protocol prefix (HTTP:// or HTTPS://) and the name of the connector that you defined in DNS for the load balanced address of your connector. For example, if your connector name is https://connector.contoso.com, your configuration will look like the following picture:
After IRM is enabled on a SharePoint farm, you can enable IRM on individual libraries by using the Information Rights Management option on the Library Settings page for each of the libraries.
Configuring a file server for File Classification Infrastructure to use the connector
To use the RMS connector and File Classification Infrastructure to protect Office documents, the file server must be running one of the following operating systems:
Windows Server 2016
Windows Server 2012 R2
Windows Server 2012
To configure file servers to use the connector
Make sure that the file servers are authorized to use the RMS connector, by using the RMS connector administration tool and the information from the Authorizing servers to use the RMS connector section. This configuration is required so that your file servers can use the RMS connector.
On the file servers configured for File Classification Infrastructure and that will communicate with the RMS connector, do one of the following:
Run the server configuration tool for Microsoft RMS connector. For more information, see How to use the server configuration tool for Microsoft RMS connector in this article.
For example, to run the tool locally to configure a file server running FCI:
Make manual registry edits by using the information in Registry settings for the RMS connector to manually add registry settings on the servers.
Create classification rules and file management tasks to protect documents with RMS Encryption, and then specify an RMS template to automatically apply RMS policies. For more information, see File Server Resource Manager Overview in the Windows Server documentation library.
Windows Server Rights Management Services
Next steps
Now that the RMS connector is installed and configured, and your servers are configured to use it, IT administrators and users can protect and consume email messages and documents by using the Azure Rights Management service. To make this easy for users, deploy the Azure Information Protection client, which installs an add-on for Office and adds new right-click options to File Explorer. For more information, see the Azure Information Protection client administrator guide.
Note that if you configure departmental templates that you want to use with Exchange transport rules or Windows Server FCI, the scope configuration must include the application compatibility option such that the Show this template to all users when the applications do not support user identity check box is selected.
You can use the Azure Information Protection deployment roadmap to check whether there are other configuration steps that you might want to do before you roll out Azure Rights Management to users and administrators.
To monitor the RMS connector, see Monitor the Azure Rights Management connector.